This report is done by Mr. Anil Shrestha as a requirement for his MSC-IT degree.
Abstract
In today’s world technology is growing faster and the possibility become beyond the expectation. So, the world is changing into Computer, AI and Internet. Internet have broken the barrier of the computer and now the data and the security is the vital things. Data is the core most important source of this world and to obtain that data people have been threat in this platform as well. Internet have increased the possibility and possibility generate the threat. Now increase in the threat different type of threat can be found and one of them is Distributed Danial of Service attack (DDoS).
The main propose of this project is that the Distributed Danial of Service attack (DDoS) have impact in various sector. This report will help to know about DDoS and their attack on the different platform and the seriousness of the attract on the different cases. The case study will show the mitigation and the explain the preventive measures on those cases.
Table of Contents
Introduction……………………………………………………………………………………………………………..1
General Introduction …………………………………………………………………………………………………1
Danial of Service Attack (DoS) ………………………………………………………………………………….1
Distributed Danial of Service Attack (DDoS) ………………………………………………………………2
Problem Background…………………………………………………………………………………………………3
Current Scenario ………………………………………………………………………………………………………3
Literature Review……………………………………………………………………………………………………..4
Critical Analysis……………………………………………………………………………………………………….6
Case Study 1: DDoS Incident Report on GitHub ……………………………………………………………6
Background ……………………………………………………………………………………………………………..6
Issue Identification ……………………………………………………………………………………………………6
Mitigation……………………………………………………………………………………………………………….7
Summary…………………………………………………………………………………………………………………8
Case Study 2: DDoS attack on Google 2017………………………………………………………………….9
Background ……………………………………………………………………………………………………………..9
Issue Identification ………………………………………………………………………………………………….10
Mitigation……………………………………………………………………………………………………………..10
Summary……………………………………………………………………………………………………………….10
Conclusion …………………………………………………………………………………………………………….11
References ……………………………………………………………………………………………………………..13
Table of Figure
Figure 1: Danial of Service Attack ………………………………………………………………………………….1
Figure 2: Distributed Denial of Service Attack ………………………………………………………………….2
Figure 3: GitHub DDoS attack ……………………………………………………………………………………….7
Figure 4: Google DDoS Attack ………………………………………………………………………………………9
1. Introduction
General Introduction
Danial of Service Attack (DoS)
Danial of Service Attacks (DoS) is the cyber-attack that reduce the accessibility of the user on the computer. The attacker attack through the bandwidth of the victim. In dos attack attacker send large amount of network traffic through the network address where the buffer is overflow and the attacker try to get the loop hole of the user to enter the network of the user where they attack and make restrict the user form the access. Danial of Service Attacks can disturb the large amount of the network without knowing of attacker. Single dos attack can affect the large number of networks with in an organization.
There is different type of DoS attack.
➢ Buffer Overflow
➢ Bandwidth Attack
➢ Teardrop Attack
➢ Physical Infrastructure DoS ➢ SYN Attack
➢ P2P Attack

Distributed Danial of Service Attack (DDoS)
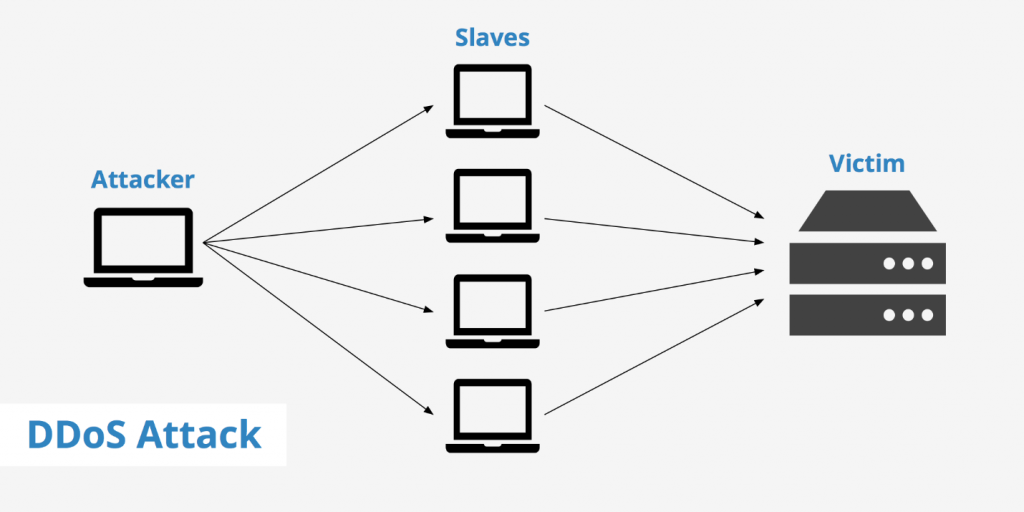
Distributed Danial of Service attack (DDoS) is done by the multiple arrays of the computer. DDoS is the upgraded form of DoS attack. Attacker attack from different location using many systems. DDoS attack is faster than the DoS attack because this attack is done by the multiple and the chance of breakthrough is high and faster. Due to multiple attack the change of blockage is less on this attack along with this the attacker is quite untraceable to the user. In this attack the attacker Bots attack at the same time which make the victim vulnerable towards the attacker. (cloudflare, 2022)
There is different type of DDoS attack.
➢ Volumetric Attacks
➢ Fragmentation Attacks
➢ Application Layer Attacks
Problem Background
The risk of cybersecurity is increasing day by day. There are various type of threats that are currently being eliminated and threat that are being executed. Among all those threats the Distributed Denial of Service (DDoS) Attack is one of them. This threat has been carried out by the attacker to the user or the company. In this type of attack the multiple arrays of the user attack on the user and the user data will be compromised. The attacker has cost the damage and the organization which compromise their data and great lose need to bare by the organization. The attacker uses DDoS attack by attempting to enter in server by the help on multiple networks and the attacker find the weak point to enter on client device. This attack chose the network traffic for their victim. This attack is performed in several time to the several big companies.
Current Scenario
Distributed Denial of Service (DDoS) Attack has caused the harm on the organization either in financial or the data loss. This attack needs to be detected and mitigate for the safety of the organization. The DDoS attack has and multiple arrays of the attack that perform on the client. DDoS atter have targeted the difference attack on the user and the user site is being loosed through it. The mitigation of the problem is performed by the different part and it can be decreased by the proper layered of the protection.
2. Literature Review
(Haydari & Yilmaz, 2018) Discusses about Real-Time Detection and Mitigation of DDoS Attacks in Intelligent Transportation Systems. They talked about traffic and attack model and Online Discrepancy Test. They also developed method quickly for immediately detecting low-rate DDoS attacks, identifying attack locations, and mitigating the attack by restricting data transmission from attack locations. They talked about Road Side Units (RSU) are more because of the smart infrastructure has been connected. They figure out the attack model where the VANET is being highly targeted by sending high volume of the data. After that simulation process is carried out as a result two different component were compared and the proposed method has low rate of attack. The extensive method has low rate of data traffic attacks.
(Sohail & Hayat, 2009)The authors have talk about the corporate defense against DDoS using GOSSIP protocol. Author explains the process to delay the attack and monitor the attack by network traffic. Omnet++ with version 4.0 is use to defense the attack. The process is to simulate every packet with node 2 will filter all those packets to the ongoing traffic, which then released unharmful packet and discarded the attack packets. This process worked as the researcher has planned and the execution of the project is successful. Author also found that the GOSSIO strategy is mover effective with the gossip node. This eliminates the threat with the overhead sharing.
(NSFOCUS, 2017)Distributed Denial of Service (DDoS) Attack an economic prospective have concluded that the cost factor can affect the DDoS attack on the organization. The organization is vulnerable because of the amount that the organization invest on their security which include the cyber-attack. The author explains the cost of this security will put a direct or indirect impact on an organization. The impact of the attack determines the cost of the organization. The threat of the modern DDoS attack increases the possibility of expected outcome for that the data of these attack should be stored and evaluate by ROI of DDoS protection solution. Different scenario is being executed regarding the cost of the DDoS on an organization. In Service Disruption in Online Retail, Data Theft, Service Disruption in Software Company.
(Mirkovic & Reiher, 2004)A taxonomy of DDoS attack and DDoS defense mechanisms. This report helps in counter measure of the problem we are facing. The attacker is exchanging the code for the attack which make other organization vulnerable. This report shows the community to communicate on the attack and discus on the problem and come up with the proper solution. This taxonomy will help to create the common platform for defense on the upcoming attacker which will be way mor easier on the future to prevent the previous attack and make perfect community to defense and stand on upcoming attack.
(kumarasamy & Asokan, 2011)Distributed Denial of Service DDoS Attack Detection mechanism provide the defense system on the DDoS attack. This method first provides the defense and stop the traffic of the unrecognized source of data. Then validate that source from the client server after that the un valid source is unrouted and conform the source of the attacker which help to detect the DDoS attacker.
3. Critical Analysis
Case Study 1: DDoS Incident Report on GitHub
Background
GitHub is one of the leading platforms where many coders and developer use their skill and provide the solution to the code that are difficult. This platform gives the service where developer can develop their code and can ask query for the problem that are need to be solved and the other users with the give their idea or code to another one. As this is an open source the probability of getting cyber threat is higher and the company is more concern about those scam or attacker. The company has huge amount of data that need to be protected from those attackers. The attacker may be from various part and can attack on this by different means of platform.
As the open platform the risk of the attack is higher than others. Cyber Security is the most concern part of the company because the company can run problem into user if the data is compromised. So to stop from that various data security is being used on the platform. Among the different part of the attacker, we are talking about the attack that happened on the 2018 on the GitHub, the attack was Distributed Denial of Service (DDoS) Attack. This attack was done on the company by creating the huge amount of traffic on the company site which leads site to keep it down for certain time.
Issue Identification
This issue was identified on the Friday 28th 2018 from 17:21 to 17:30 time. In this attack the UTC network monitoring system detected them network transformation to the external network from the organizations network. This attack was the amplification of the Memcached based approach. On this attack the attacker used the multiple arrays of the network. The Autonomous system ASNs from the large amount of the network with the tens and thousand of the unique end point is being detected. This attacker uses the growth factor of the Memcached on this approach. During the attack the GitHub website was down for approximately 5 min in time. The attacker main goal was to stop the site and the decline the access on this site. (GitHub, 2022)
Mitigation
The attack was happened and the decisions was taken to move the traffic to the Akamai. GitHub was able to mitigate problem due to their security defense system where they have used the DDoS protection service. This protection helps to notify the user within the 10 min of the attack due to which the victim can react too quick. GitHub use the Akamai to provide the additional edge network for their client, which is huge number in capacity. The edge network from akamai is used to mitigate the problem of this attack. (medium, 2022)
Akamai architecture have different type of defense system that are being use and one of them is edge defense system of akamai. This defense system helps to distribute the proxy reverse to the traffic with via port 80 and 443. In this process the client hosts the platform and direct to this edge platform. In the all-network layers are dropped down with in a zero second SLA. This makes edge defense unbreakable due to these protection layer where all the threat is eliminated. (akamai, 2022)
Summary
GitHub is the platform of the developer where all source of data is shared related to the programming and IT. This site is being attacked various time. Among those attack 28th February 2018 attack is one of them and in this attack the attacker created huge amount of traffic on the GitHub site this attack was executed for about 5 min. During this time the site was down. The website is being host on edge defense system of akamai. After that the site is recovered and the attack threat was eiminated.
Case Study 2: DDoS attack on Google 2017
Background
Google is the famous search engine available in today’s world. This company is one of the biggest and revolutionary company in the field of the technology. As this platform is the largest search engine the amount of user is more than in another site. Access on this search engine is easy and simple. Which make it look vulnerable to the attackers. As the company is bigger and the public based the company need to invest more in cyber security. This site is the most popular in the world and the attack on this site highly possible but the success rate is compared and filtered by the security that has been used by this company. Company needs to protect the data and the site from the attacker. Among the various type of attack, Distributed Denial of Service (DDoS) Attack is the one of the attacks that happened on google 2017 September. This attack was the largest attack that are being recorded thill date by the google from the Distributed Denial of Service (DDoS) Attack. Google not one face this attack but it also successfully mitigates those attack with their cyber security process.
Issue Identification
The issue of the google was detected on the September 2017. This is the biggest Distributed Denial of Service (DDoS) Attack that the google claim to have on them. The traffic of the attack was the largest till date which is 2.54 Tbps. Google was attacked for several time through huge amount of network that spoof 167 Mbps to around 180000 exposed. The various attack that performed was on Connection less Lightweight Directory Access Protocol (CLDAP), DNS and SMTP. All this send the larger respond to the google which increase the amount of traffic that are being used by the attacker. This attack is the largest attack and the incidents was recorded by the google. As this attack was Google Threat Analysis Group (TAG) conform that the attack was performed from China. They confirmed that the attacker uses 4 different Chinese IP from China. (zdnet, 2022)
Mitigation
The Distributed Denial of Service (DDoS) Attack was performed by the attackers on September 2017. This attack has been mitigated by the Google Threat Analysis Group (TAG). The attacker attack from the different network to spoof 167 Mpps (Millions of Packets Per Second) to 180000 exposed. This was mitigated due the high defense system of the google. The google security. Company performed campaign for six months after the attack was detected. Google work with other network providers to eliminate the threat and trace the source of the attacker. To trace the source the company, work with network provider and search all the spoofer and their network address. In this way google can mitigate the threat from the DDoS and the higher ever recorder attack was eliminated without any ham on the company and the user. DDoS security layer of the google is sufficient for the threat to eliminated and the attacker to stop. (Google, 2022)
Summary
Google search engine is the most popular among us and this was attack by the attacker. DDoS attack was performed and google was successfully identify and mitigate the threat. This threat was now being eliminated and the source of the attack is also found. The security layer that googles used was good enough to prevent from that threat.
4. Conclusion
As technology getting bigger and better the threat of the data is also getting bigger. The Information and Technology is the key to future world and as every good thing have their good impact this field is also have and negative impact on the society. All this is because of the threat of the attacker on this place is not seen and the detection to those threat need professional. In todays world every company need and IT for the support because slowly all the company and the business is being digitalized. So, this creates a threat potential to the different parties. There is different type of attack that are being carried out in the internet and the one of them is Distributed Denial of Service (DDoS) Attack. This attack is performed by the various network to the victim and make victim site weak and crash those sites, which means that the user cannot use that side due to the heavy traffic on that site.
As we research in literature review there are different process and the factor where the DDoS can make harm to. The economy of the company and the data of the company is directly or indirectly affected by the DDoS attack. Different article and the journal have published on the DDoS attack. The defense method on this DDoS attack, Real time mitigation of the DDoS attacks. Different after provide different method of the prevention of the DDoS attack.
On this report the case study is done on two different DDoS attack. One is the attack that happened on 28th February 2018. In this case the attacker attacks the open-source platform of the code learner GitHub was attacked and the side was down for up to 5 min. during this time duration the attacker send huge amount of the traffic and caused the site go down. This site was then hosted from edge defense system of akamai which has the capacity to eliminated the threat of the DDoS attack. The whole layer of protection on use on this site help GitHub to eliminate the threat.
Second case study was done on the Google DDoS attack on 2017, this attack was performed by the various network. This is recorded as the largest attack on the google till date. This attack was unsuccessful. Google use different network agency to track the threat and it was recorded that the source of the threat came from the China with 4 different IP. This proved that the google have the best security to eliminate the threat on the DDoS attack.
Distributed Denial of Service (DDoS) Attack is one of the threats that can be eliminated by the protection layer. This threat can cause harm to the organization so to avoided this threat the user or the organizer need to provide the security.
5.References
akamai, 2022. What is A DDoS Attack?. [Online] Available at: https://www.akamai.com/our-thinking/ddos [Accessed 15 May 2022].
cloudflare, 2022. what-is-a-ddos-attack. [Online]
Available at: https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/ [Accessed 15 May 2022].
GitHub, I., 2022. February 28th DDoS Incident Report. [Online] Available at: https://github.blog/2018-03-01-ddos-incident-report/ [Accessed 14 May 2022].
Google, 2022. Exponential growth in DDoS attack volumes. [Online]
Available at: https://cloud.google.com/blog/products/identity-security/identifying-and- protecting-against-the-largest-ddos-attacks
[Accessed 15 May 2022].
Haydari, A. & Yilmaz, Y., 2018. Real-Time Detection and Mitigation of DDoS Attacks in Intelligent Transportation Systems, Tampa, Florida 33620: University of South Florida.
kumarasamy, S. & Asokan, D., 2011. DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM. International Journal of Computer Science, Engineering and Information Technology (IJCSEIT), Vol.1, No.5(2011), pp. 38-49.
medium, 2022. how-github-survived-the-biggest-ddos-attack-ever-recorded. [Online]
Available at: https://medium.com/technology-hits/how-github-survived-the-biggest-ddos-attack-ever-recorded-6907ba6f5c98 [Accessed 15 May 2022].
Mirkovic, J. & Reiher, P., 2004. A Taxonomy of DDoS Attack and DDoS Defense Mechanisms∗. ACM SIGCOMM Computer Communication Review, 34(2)(2004), pp. 39-53.
NSFOCUS, 2017. DISTRIBUTED DENIAL-OF-SERVICE (DDoS) ATTACKS: AN ECONOMIC PERSPECTIVE, Santa Clara, California: NSFOCUS.
Sohail, I. & Hayat, S., 2009. COOPERATIVE DEFENSE AGAINST DDoS ATTACK USING GOSSIP PROTOCOL, Blekinge Tekniska Högskola: Blekinge Institute of Technology.
tutorialspoint, 2022. Denial-of-Service (DoS) Attack and its Types. [Online]
Available at: https://www.tutorialspoint.com/denial-of-service-dos-attack-and-its-types [Accessed 14 May 2022].
zdnet, 2022. Google says it mitigated a 2.54 Tbps DDoS attack in 2017, largest known to date. [Online]
Available at: https://www.zdnet.com/article/google-is-using-machine-learning-to-stop-ddos- attacks[Accessed 15 May 2022].