This report is done by Mr. Aniket Hyouju as a requirement for his MSC-IT degree.
Abstract
The current world revolves around encryption. Encryption ensures that every time you make a phone call, purchase anything with a credit card at a store or on the internet, or even obtain cash from an ATM, the transaction is confidential and secure. Nowadays people are more over digital payment then hand to hand payment which is impossible without encryption. A data for a user is most vulnerable and valuable thing for him/her so encryption protects data content rather than preventing unlawful data transmission interception or access. Intelligence and security agencies utilize it, as well as personal security software that protects user data. Encryption allows you to set up several important forms to successfully manage it, including a password that prevents leaks to other devices. In this report we have discussed about the use of encryption in past years and different method used as encryption methods. With the progression of time, the encryption algorithm has also evolved in a positive way. However, there are several threats that have arisen with the time so strong encryption is needed for those problems.
The main purpose of this report was to figure out the impact of failure of data encryption and vulnerability of different encryption methods. Some security issues exist, such as encryption providing a false impression of security, the user losing the password or key to an encrypted file, and therefore losing access to the file. We have discussed about decryption method of historical ciphers which was time consuming. Some of the methods of mitigation and causes are discussed below from the case studies.
Keywords: Encryption, cryptography, cipher, decryption, AES, DES, TDES
Table of Contents
Introduction………………………………………………………………………………………………………………….. 1
General Introduction …………………………………………………………………………………………………. 1
Problem Background …………………………………………………………………………………………………. 2
Current Scenario ……………………………………………………………………………………………………….. 3
Literature review ………………………………………………………………………………………………………….. 3
Critical Analysis ……………………………………………………………………………………………………………. 4
Case Study 1: Veeam case of customer records compromised by unprotected database . 4
Background ……………………………………………………………………………………………………………. 4
Objectives ………………………………………………………………………………………………………………. 5
Issue Identification …………………………………………………………………………………………………. 6
Mitigation ………………………………………………………………………………………………………………. 7
Case study summary ………………………………………………………………………………………………. 7
Case Study 2: Marine Corps details exposed due to unencrypted email fails ………………… 7
Background ……………………………………………………………………………………………………………. 7
Objectives ………………………………………………………………………………………………………………. 8
Issue Identification …………………………………………………………………………………………………. 8
Mitigation ………………………………………………………………………………………………………………. 9
Case study summary …………………………………………………………………………………………….. 10
Conclusion ………………………………………………………………………………………………………………..11
References ………………………………………………………………………………………………………………… 12
Table of Figure
Figure 1: Encryption process ……………………………………………………………………………………………. 1
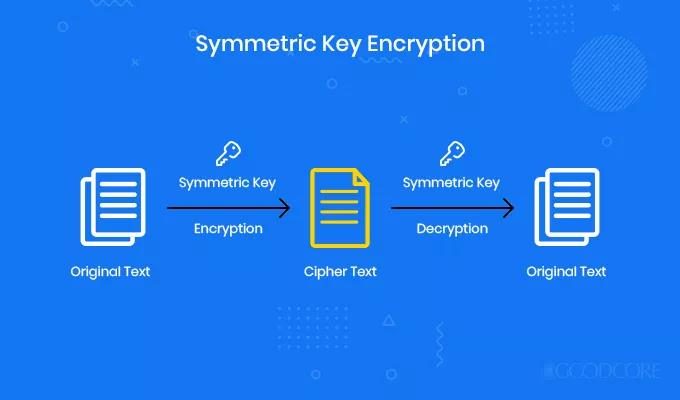
Figure 2: Symmetric Encryption……………………………………………………………………………………….. 2
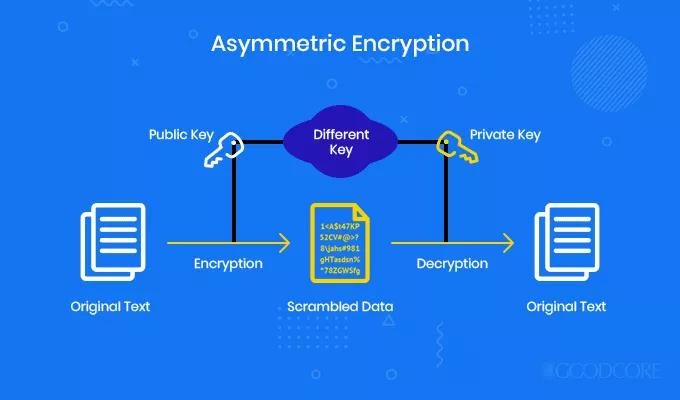
Figure 3: Asymmetric Encryption …………………………………………………………………………………….. 2
Figure 4: Veeam backup ………………………………………………………………………………………………….. 5
Figure 5: Database protected by veeam……………………………………………………….. 6
Figure 6: A US Marine Assigned to cyber security……………………………………………………………… 9
Figure 7: Encrypted email system……………………………………………………………………………………. 10
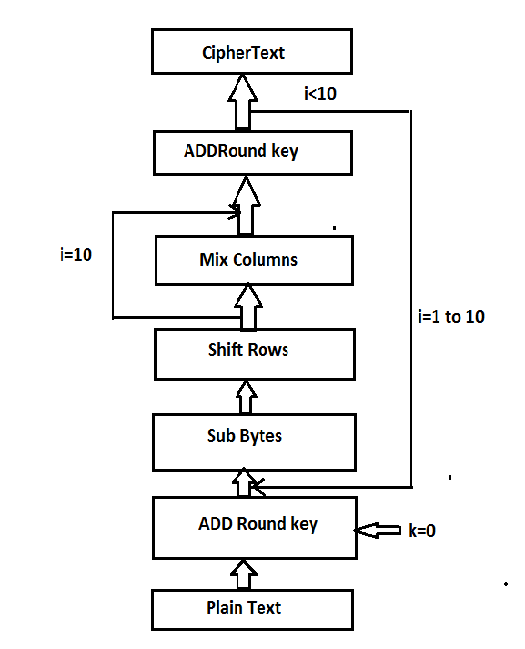
Figure 8: Advance Encryption Standard in modern age ……………………………………………………… 11
Table of Abbreviations
Abbreviation
TDES: Triples Data Encryption Standard
AES: Advanced Encryption Standard
DTS: Defense Travel System
DOD: Department of Defense
RSA: Rivest-Shamir-Adleman
FPE: Format Preserving Encryption
TCP: Transmission Control Protocol
NIST: National Institute of Standards and Technology
Introduction
General Introduction
Data encryption is a technique used to prevent unauthorized access to encrypted data. It works by sending a message with a cryptographic key to an authorized user. Encryption solutions must be sophisticated as well as quick enough to safeguard data transmission lines. Data has become the world’s most valuable assets. For protection of communication and our data, encryption are based on complicated algorithms and use combination of encryption keys of symmetrical and asymmetrical system. Good algorithms and protocols with good system design and implementation are necessary. Some of the categories of encryption are
- Triple DES(TDES)
- Advanced Encryption Standard(AES)
- Rivest-Shamir-Adleman(RSA)
- Blowfish
- Twofish
- Format Preserving Encryption(FPE)
Where I will be focusing on AES and RSA. AES uses a symmetric encryption system and can support up to 256 bit keys. Whereas, RSA uses asymmetric cryptography technique that operates with two keys, i.e. Encryption with public key and Decryption with private key. It can support up to 2048 bit keys which will consume more time while processing and is consider as one of the best cryptography techniques.
I will be focusing on AES and RSA. AES uses a symmetric encryption system and can

Problem Background
The most common method of defeating encryption nowadays is brute force, which is attempting various keys until the proper one is found. Of course, the key’s duration affects the attack’s legitimacy by determining the number of keys that may be generated. Encryption may create problem in a well-known security products, let’s take an example of patient records. A clever state actor may steal an administrator’s credentials, decrypt the data, alter your blood type, encrypt it again, and destroy the proof of their actions. Then, all of a sudden, you’re dead, and no one knows what happened. It’s important to note that the encryption strength is proportional to the key size, but the amount of computing power required to do the computation grows as the key size grows. There are multiple sorts of cryptanalytic attacks and that any given method would need the attacker to do more work to crack it while employing one assault than another complicates the problem and makes it less subsumable into a single strength metric. Using the old encryption ciphers like DES in modern time may be a problem, which was used by U.S government around 1970s for protecting binary-coded data during transmission and storage of classified information in computer systems and networks, as well as on a case-by-case basis. The SWEET32 Issue, which has been reported in two CVE Issues, is a problem with 3DES. It belongs to a Family of initially weak Ciphers since its basic Cipher Depth is 64Bit. It should no longer be utilized, given the current state of security in 2017 and the likelihood of it being cracked more frequently and readily.
Current Scenario
Cyberattacks are always changing, requiring security experts to devise new tactics and techniques to combat them. There are several variations, with 128-bit, 192-bit, and 256-bit encryption being the most prevalent. , 256-bit encryption is the safest option among these 3. Today, AES is a widely used and trusted technology. Governments including the US National Security Agency have approved encryption standards based on the AES block cipher, which encrypts a fixed-length group of bits. C, C++, java, JavaScript and python programming have been using AES libraries. Disk encryption systems like BitLocker and FileVault employs AES. AES is mostly used by password managers including LastPass and KeePass, as well as messaging apps such as WhatsApp and Facebook Messenger. All Intel and AMD CPUs provide the AES instruction set. (Tobias, 2021)
Literature review
(McDonald, 2009) In this report the author has talked about encryption and cryptography used in different generations. Worldwide web has allows people to communicate mail, information through digital medium. He believes that, as a result of this contemporary communication system, individuals will be able to find better techniques to secure their precious information by knowing encryption. A country’s defenses and ability to live in a hostile environment might be strengthened by mastering encryption. Individuals who have a basic grasp of encryption can assist secure private data and information.
(Pandya, et al., 2015) This journal contains of historic briefing of Encryption, they have mentioned that the most advanced and safe encryption technology has proven to be AES. They have mentioned about using symmetric and asymmetric key system for encryption. They also have talked about pseudorandom where they have discussed about increasing security by generating a random but repeatedly which supplies the system with a great degree of security.
(Nissar, et al., 2019) The execution of existing encryption algorithms such as AES, DES, and RSA was investigated. They’ve described efficient AES additions (such the Dynamic characteristic of S-Box, Key Dispersion Technique, and hashing technique) to bring it up to date in terms of security as technology evolves. It might provide a viable alternative to current AES implementations. The algorithm is rather remarkable and warrants further thought.
(Chen, 2021) This journal consists of how to efficiently gather and use industrial accounting statement data through scientific and effective financial analysis methodologies has become a key topic of widespread concern in all walks of life in the new era for accounting information. And also talks about the weakness of DES algorithms that is its small key length which makes it vulnerable to exhaustive assaults. In comparison to the traditional DES method, the 3DES encryption algorithm has not evolved significantly over time. The DES algorithm has been enhanced to promote security and reliability. In this article the author also mentioned about encrypted QR code which is obtained after a sequence of processes is sent straight to the receiver for decryption, rather than being printed out. Because the subsequent activities are carried out by scanning the printed QR code, relevant research on QR code identification may be carried out as part of the follow-up work.
(Kenekayoro, 2010) This journal contains 34 years of overview of data encryption, the first encryption system to fulfill the standards of National Institute of Standards and Technology’s for an encryption system. To avoid brute force assaults, the DES has been extended to the TDEA. TDEA, along with AES, is the encryption technique utilized in industry today. The DES is still safe and used today, despite the invention of a new symmetric encryption scheme (AES). Although upgrading to AES is encouraged, the move from DES to AES will be simple because it is not required.
(Abolade, et al., 2021) In this journal authors have talked about the difference between encrypted data and unencrypted data transfer through TCP across the secured network. Transmission times vary depending on the amount of the data that was encrypted. Data that was encrypted took longer to transport over the network. Furthermore, with unencrypted data, the network transfer time remained stable as data size rose. With non-encrypted data, transfer time was shown to be consistent as data size rose, however encrypted data with the same set of data size had inconsistent data size increases owing to padding.
Critical Analysis
Case Study 1: Veeam case of customer records compromised by unprotected database
Background
Switzerland-based Veeam bills itself as the “world leader in intelligent data management,” offering “Hyper-Available” data management solutions that combine traditional data backup and recovery with current cloud settings. The unsecured MongoDB server was indexed on August 31 and remained open until September 9. Veeam’s data was spread across 200 gigabytes in the exposed database. Customer records, including names, email addresses, and some IP addresses, were among the data. (Data management firm Veeam mismanages own data, leaks millions of records, 2018)
Objectives
Passwords and user names are a somewhat insecure method of safeguarding private access. Furthermore, attackers have a greater chance of acquiring access to internal systems if a company does not keep total control of the private keys that regulate access. Using encryption algorithm may be helpful in these situation. Shodan, a search engine that may be used to locate Internet- connected devices and, in some situations, open systems, was utilized to make the finding. The security researcher is alluding to a campaign known as Mongo Lock, which is now targeting MongoDB servers that are open and unprotected. These servers are highly targeted by the attackers, captures all of the data on them, and then demand a ransom from victims in exchange for their data.
Issue Identification
Records were cached between 2013 and 2017, and the database was thought to be tied to Veeam’s design rather than Marketo’s infrastructure. Air Canada warned customers in August of a data incident that might have compromised the passport information of up to 20,000 passengers. According to the carrier, unusual login behavior was detected in systems related to the Air Canada mobile app between August 22 and 24, and while the attack was quickly shut down, personal information, may have been compromised. After TechCrunch contacted Veeam of the mishandling, the server was taken offline after three hours. Peter McKay, Veeam’s co-chief executive, wrote about the issue in a blog post on September 13th “This single marketing database holding marketing records (that may include names, e-mail addresses, and IP addresses) was left accessible and exposed due to human mistake during network maintenance. Unauthorized third parties had access to the database, which was not easily accessible.”
Mitigation
Big firms’ cyber security policies and procedures should be revised on a regular basis. Undertaking a more thorough investigation, and depending on our findings, we will take necessary action.
Some mitigating security rules and procedures are needed to prevent future data breaches/server human mistake i.e.
- Regular Risk Assessments – Conduct vulnerability assessments to identify and remediate any modifications or new data security concerns. Consider all factors, including as data storage and employee remote access, and make sure rules and processes are in place.
- Encryption and data backup – Personal information particularly that stored on business laptops should be encrypted at the very least. Data may be backed up to distant services through the Internet instead of utilizing backup tapes that can be lost or stolen.
- Verify that suppliers and partners adhere to strict data security guidelines – When collaborating with other firms that may handle your customers’ data, ensure sure they have proper data protection mechanisms in place as well.
- Up-to-date Security Software – Ensure that software is updated and patched on a regular basis to avoid hackers exploiting security flaws.
Case study summary
From the case study, we can see that some big data storing company can also make mistakes regarding storing personal data of an individual. Veeam is consider as one of the best for developing backup software and data protection software. But we found that due to some human error some data can be breached and can be visualized to other.
So implementing best encryption may be the solution for the problem which includes work laptops and data issued to an individual.
Case Study 2: Marine Corps details exposed due to unencrypted email fails
Background
Unencrypted emails misfires is similar to phishing emails which is an internet fraud in which a cybercriminal sends an email that looks to be from a real firm and requests sensitive information from the consumer. The Defense Travel System (DTS) of the US Department of Defense (DOD)
sent an unencrypted email with an attachment to the incorrect distribution list in January 2018, containing the personal information of thousands of Marines, sailors, and civilians, including bank account details. The personal information of about 21,426 Marines, sailors, and civilians was exposed through email sent by the DTS within the official unclassified Marine domain and also to some civilian accounts. Criminals or businesses can utilize personal information to steal identities, perpetrate bank and credit fraud, or engage in phishing scams. ISIS published a ‘death list’ of 41 Marines and sailors in 2015, based on information from publicly available online forums and social media profiles. (Snow, 2018)
Objectives
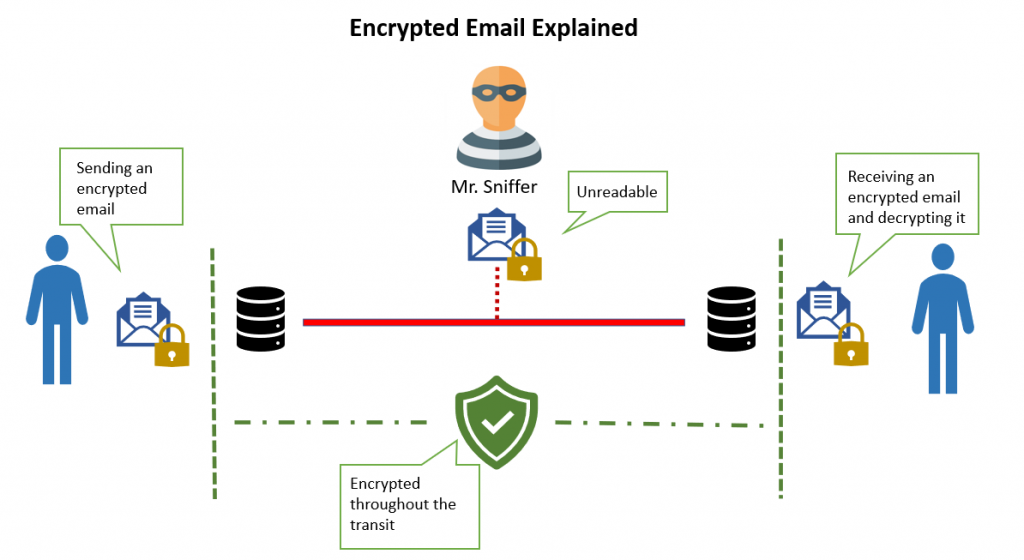
Cybercriminals can put themselves between two email servers to intercept and read emails if firms do not use effective encryption. Senders must be more careful for these kind of misleading mistakes which affect thousands of innocents. Mishandled data includes home addresses, postal addresses, and emergency contact information, in addition to incomplete banking details. Sending sensitive personal data via unencrypted connections is effectively an open invitation to hackers. The importance of email encryption is that it protects you from a data intrusion. Because the hacker can’t read your communication because it’s encrypted, they won’t be able to do anything with it. If the email which was sent by mistake was encrypted then there won’t be much of the problem. The Marines intend to make improvements in the future to better protect personally identifiable information.
Issue Identification
Major Andrew Aranda mentioned that issue was immediately discovered, and email recall processes were put in place to restrict the number of accounts that got it. The Marine Corps takes the privacy and personal data of individual Marines extremely seriously, and to minimize the amount of email accounts that would receive the spam, the Marines instituted email recall processes. They also stated that they intend to take further security measures in the future. They have procedures in place to avoid the unintentional or purposeful leaking of such information. Officials think the leak was unintentional, and Aranda said the event was still being investigated while victims were being alerted. This type of leaked military information, particularly information on active duty troops, can be used to steal identities, impersonate victims, and commit financial fraud. Aranda said that they are taking the protection of individual Marines’ private information and personal data extremely seriously, and we have procedures in place to avoid the unintentional or purposeful publication of such information.
Mitigation
Defense travel system should be careful for these kind of activities. An encrypted email would have been a good option rather than unencrypted email it won’t affect in mass. Some necessary action for protecting these kind of actions are-
1. Use End-to-End Encrypted Protected Emails – End-to-end encryption encrypts all data before it is transferred to a server, using an encryption key that is not known by the server. When there is a breach at the server level, encryption helps to safeguard your emails from data breaches.
2. Limit Administrator Permissions – Insider threats, such as targeted hacking via phishing operations, can readily compromise an administrator account despite typical security settings. Privilege escalation attacks can be mitigated by restricting administrator account privileges and securing the email implementation against suspicious third-party meddling.
Case study summary
In this case, we learn about phishing emails, and how an unencrypted email can be a thread if it reaches wrong address. A US marine defense system can make such a mistake mistake so the data must be carried with encryption, and be careful with email address and URL. Due to some human error such mistakes can happen in large organization more than 21000 private information got leaked.
So use of end to end encryption may be solution to these human error and maybe be more careful before sending email and to avoid this issue, make any necessary adjustments to properly safeguard how we acquire and retain data.
Conclusion
Modern problems require modern solutions, encrypted algorithms are used to communicate in a secure manner in today’s environment, and encryption is a critical technique for safeguarding data in computer systems. Computer systems are now highly networked and available from anywhere in the globe thanks to the creation of the Internet. With some security there arise some problems such as encryption may provide false sense of security, user may loss the password or key of encrypted file which leads user to lose access to the file. Encrypted data may be hacked or decrypted with enough time and computer resources, revealing the original information. Hackers prefer to steal encryption keys or intercept data prior to or after encryption or decryption. The most common method of hacking encrypted data is to add an encryption layer using an attacker’s key. In some cases we have learned about the importance of encryption needed for a file in order to be protected if any human error happens like leakage of data and server. Some big data companies and defensive system may make those mistakes so encryption key is a must in these kind of cases. In modern era the most used encryption system is AES as well as it is well protected. The NIST has withdrawn DES in its entirety. Only as a component function of the Triple Data Encryption Algorithm is it allowed to be used. Triple DES is mostly recommend by the US Department of Commerce for protection of unclassified data then DES algorithm. Selecting the appropriate persons to get access to is a straightforward way to avoid odd procedures.
Hence to get secure data only encryption is not enough, human effort with encryption is needed for a secure file. A regular check up on file must be needed. An encrypted file has a high level of ownership and social security.
References
Abolade, O. et al., 2021. Overhead effects of data encryption on TCP throughput across IPSEC secured network. Scientific African, 13(13), pp. 1-6.
Binary Blogger, 2021. The 5 Advantages of High Secure Files. [Online]
Available at: https://binaryblogger.com/2021/07/02/encrypted-pdf-the-5-advantages-of-high- secure-files/
[Accessed 14 may 2022].
Chen, M., 2021. Accounting Data Encryption Processing Based on Data Encryption. Research Artical, I(4 june 2021), p. 12.
Data management firm Veeam mismanages own data, leaks millions of records (2018) Charlie Osborne.
Kenekayoro, P., 2010. The data encryption standard thirty four years later: An overview. African Journal of Mathematics and Computer Science Research, Volume 3, pp. 267-269.
McDonald, N. G., 2009. PAST, PRESENT, AND FUTURE METHODS OF CRYPTOGRAPHY AND DATA ENCRYPTION, Utah: University of Utah .
Murdock, J., 2018. U.S. Marines Email Leak Exposes Secrets of 21,000 Soldiers, Civilians. [Online]
Available at: https://www.newsweek.com/us-marines-data-breach-leak-soldier-secrets-hits- 21000-soldiers-civilians-825382[Accessed 3 march 2018].
Nissar, G., Garg, D. K. & Khan, B. U. I., 2019. Implementation of Security Enhancement in AES by Inducting Dynamicity in AES S-Box. International Journal of Innovative Technology and Exploring Engineering (IJITEE), 8(11), pp. 2364-2373.
Pandya, D. et al., 2015. Brief History of Encryption. International Journal of Computer Applications, pp. 28-31.
Snow, S., 2018. Major data breach at Marine Forces Reserve impacts thousands. [Online] Available at: https://www.marinecorpstimes.com/news/your-marine-corps/2018/02/28/major- data-breach-at-marine-forces-reserve-impacts-thousands/
[Accessed 10 may 2022].
Tobias, E., 2021. 128 or 256 bit Encryption: Which Should I Use?. [Online]
Available at: https://www.ubiqsecurity.com/128bit-or-256bit-encryption-which-to-use/ [Accessed 19 march 2022].
Tresorit, 2022. The history of encryption: the roots of modern-day cyber-security. [Online] Available at: https://tresorit.com/blog/the-history-of-encryption-the-roots-of-modern-day-cyber- security/
[Accessed 17 march 2022].
Veeam, 2022. Veeam Help center. [Online]
Available at: https://helpcenter.veeam.com/docs/one/reporter/sql_backup_job_information.html?ver=110 [Accessed 11 march 2022].