Word Count (Where Required): 2397
I confirm that I understand my coursework needs to be submitted online via Google Classroom under the relevant module page before the deadline in order for my assignment to be accepted and marked. I am fully aware that late submissions will be treated as non-submission and a mark of zero will be awarded.
Abstract:
There is substantial evolution in malware sophistication in recent days. Malware is one of the global problems nowadays. Malware has the ability to infect any electronic device. Mobile devices are more popular among users than other electronic devices. The main purpose of this study is to look into various malwares in a mobile context. As a result, in this report mobile malware is discussed in detail. Fake apps propagate mobile malware primarily outside of the Play Store, while these types of apps can also be found in the Play Store. It is quite difficult to distinguish between malicious and legitimate apps.So, to classify among a large number of apps different types of machine learning algorithms were used to classify apps between malicious and non malicious apps.This research also covers two case studies of mobile malware: the facebook stealer trojan and mobile banking malware. The background, issue identification, and mitigation of both case studies are described in this study.
This report explains the various types of malware in Android and how to identify them using various machine learning approaches. More studies are needed to improve malware detection techniques.
Table of contents:
1. Introduction 1
1.1 General Introduction
1.2 Problem Background
1.3 Current Scenario
2. Literature Review
3. Critical Analysis
3.1 Case Study 1 Facebook Stealer Trojan
3.1.1 Background
3.1.2 Issue Identification
3.1.3 Mitigation
3.1.4 Summary
3.2 Mobile Banking Malware
3.2.1 Background
3.2.2 Issue Identification
3.2.3 Mitigation
3.2.4 Summary
4. Conclusion
References
Table of figures:
Figure1: Types of malwares in android
Figure 2: Malware types
Figure 3: Facebook Stealer Trojan Craftsart Cartoon Photo Tools
Figure 4: facebook stealer trojan snap beauty camera
Figure 5: Mobile Banking Malware
1. Introduction
1.1 General Introduction
Any malicious program designed to intentionally harm or gain access to the computer system(network, server, devices or user) can be called Malware (Malicious software). Malware comes in a variety of forms. Computer viruses, worms, Trojan horses, spyware, adware, rootkits, keylogger, ransomware, wiper, and other sorts of malware are some of the common types.
Malware can infect any electronic device, including laptops, desktop computers, tablets, and smartphones. It can impact any operating system, including Windows, Mac OS X, iOS, and Android. When it comes to mobile malware, Android smartphones are more likely to be infected than iOS devices because . Attackers get access to a device’s components such as the camera, bluetooth, microphone, GPS data, accelerometer and even network connection if it is attacked. It poses a risk to corporate users and individuals as it can steal protected data, encrypt, erase information or take over computing processes and watch end users’ computer behavior.
1.2 Problem Background
Users who neglect to update their phones and others who don’t receive the update are one of the most common causes of vulnerability. Different studies show that the older phones running Android versions lower than 6.0 are more vulnerable because they are not receiving security upgrades at the moment (patches). The most recent version of Android is 12 released on October 4, 2021 includes a number of powerful privacy features. As a result, according to the Android Security Bulletin for February 2022, Android versions should be updated on a regular basis. On the other hand,the current Android version will not run on phones with lower specifications and RAM. Because vulnerabilities can be exploited once discovered, regular security updates are essential for protecting against them. There are also other vulnerabilities that have yet to be identified. Google Play protects devices and data, as well as determining PHAs (Potentially Harmful Application). It also has anti-malware protection, which is also insufficient to defend against attackers.
1.3 Current Scenario
There are two types of apps, preinstalled apps and user-installed apps.
The majority of preinstalled apps are from the original equipment manufacturer, thus they don’t have any issues. The biggest issue is user-installed apps from an illegal source. Mobile apps can be infected from a number of different places.
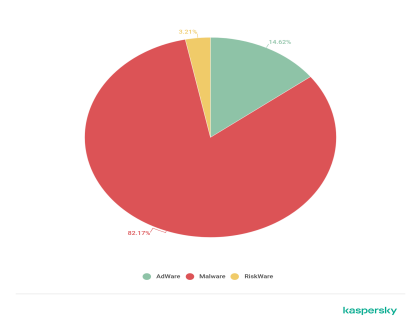
Figure1: Types of malwares in android (securelist, n.d.)
This above image shows the attack of mobile malware in mobile devices. If we divide them into types, malware(82.17%) accounts for the majority of attacks, followed by adware(14.62%). We can see the detail in the following image with the type of malware.
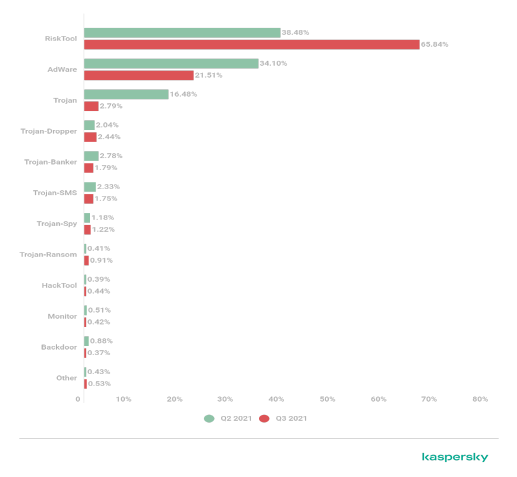
Figure 2: Malware types (securelist, n.d.)
The number of attacks is also increasing in the year 2021. It seems that risktool malwares are increasing more than any other malware.
Malware attacks can come from a variety of ways, including opening malware-infected emails, accessing unsecured wifi/urls, and sending text messages that can spread between devices. Some of the examples android malware are: Simplocker(2014), Plankton(2011), Emotet(2014), HongTouTou(2011), Brata(2019), Sharkbot(2021), AbstractEmu (2021), GriftHorse(2021) ,tanglebot(2021) etc.
Another problem is determining whether or not the app is malicious. Various machine learning algorithms and deep learning approaches are implemented, which will be explained in the following sections.
2. Literature Review
Malware is quickly becoming one of the most dangerous online threats. Once the virus is installed, attackers can use it to spy on your online activities, steal personal and financial information, or use your device to infiltrate other systems. (PaloAltoNetworks, n.d.) RATs(Remote Access Tools), Mobile Phishing, Bank trojans, Browser Exploits, Ransomware, Cryptomining Malware,Advertising Click Fraud etc are some of the common smobile malwares types that are infecting mobile devices.(crowdstrike, n.d.)
Different strategies can be used to safeguard mobile devices from malware. There are two types of checks: manual and dynamic. It’s difficult to find malicious apps among a vast number of them. As a result, various machine learning algorithms were built and tested to detect malicious apps, and those techniques were also used to determine the model’s accuracy.(Belal, 2017)
(Duraipandian and Vinoth kanna, 2019) uses machine learning models such as logistic regression, classification and regression trees, random forests, and Naive Bayes to identify malicious Android apps and compare them to existing methods. Malicious applications were identified by first installing them, then extracting features, training the above mentioned machine learning model, and classifying them by calculating precision, accuracy, F-score, true positive rate, and false positive rate.
(Colaco, Bagwe and Bose, n.d.) focuses on the Support Vector Machine algorithm for detecting android malware, (Confusion Matrix) KNN for analyzing accuracy and Decision tree for families identification. After training and testing the data, they uploaded it to a cloud engine/ cloud server where users could upload an app to see if it contained malware or not.
(Milosevic and Dehghantanha, 2017) uses two types of analysis: permission-based and source code-based, as well as two machine learning approaches: classification (to determine whether or not an app is malicious) and clustering ( to retrain classification model). In a permission-based approach, they calculated cluster instances, and in a source code-based classification, they calculated precision, recall, and f-score. They compared different algorithms for classification, such as decision tree, random forest, naive bayes, Support Vector Machine, Logistic regression, JRIp, and SVM, and found that SVM had a higher accuracy than the others. Similar other classification is used by (Afonso et al., 2014) in which Random forest produced the best results,
(Senanayake, Kalutarage and Al-Kadri, 2021) compared advantages and disadvantages among different algorithm like Decision Tree,Navies Bayes, Gradient Boosting, Regression, K-nearest neighbors, Support
Vector Machine, K-MEANS Clustering, Random Forest, Neutral Networks, LSTM, CNN, Ensemble Learning covering the latest research from 2016 to 2021.
(Xu et al., 2018) compared DroidDelver, Dodroid, Droid-Sec, CSBD, Debrin, and other existing detection techniques using Deep Learning Technique called CNN, control flow graph (CFG), and data flow graph (DFG). A similar paper (Alzaylaeea, Yerima, and Sezer, 2020) used real android devices to test their framework called DL-Droid, which also uses Deep Learning techniques, and found that the accuracy was 98.5 percent in thirty one thousand android apps, of which 11 thousand were malware and the remaining 19 thousand were other apps.
3. Critical Analysis
3.1 Case Study 1 Facebook Stealer Trojan
3.1.1 Background
We still have Android malware in 2021 that can steal data and information from our devices. These trojans are designed to steal user credentials by impersonating the original login authorizer. User’s login usernames and passwords were obtained by using a similar layout to Facebook’s login page, where users entered their credentials assuming they were real one.
3.1.2 Issue Identification
The Face Stealer Trojan collects Facebook account’s data, including email and IP address, using a login page that looks like Facebook’s official login page. When the user clicks to sign in, a login with Facebook screen will appear. The malicious apps that contain this trojan will not work until the user signs in. Following that, the user’s login and password are collected by malicious javascript code and transferred to their database or server which owns the application. The face stealer trojan has been discovered in a variety of apps.
Craftsart Cartoon Photo Tools is one of the apps that uses Face Stealer, and when we open the app, it takes us to a sign-in page. If we provide our login information, they will misuse our information on any sector they want.
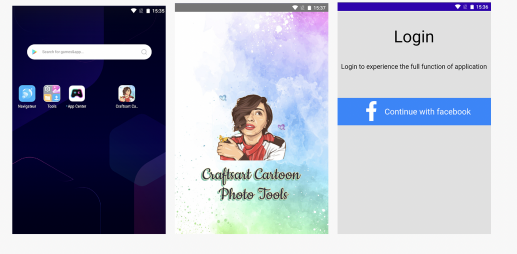
Figure 3: Facebook Stealer Trojan Craftsart Cartoon Photo Tools(crowdstrike, n.d.)
More than 1,000,000 people had downloaded the app from the Google Play Store. The app was later removed from the Play Store after a face stealer virus was discovered in it. The application is no longer available for download. This trojan can be injected into similar other apps like shown in figure below.
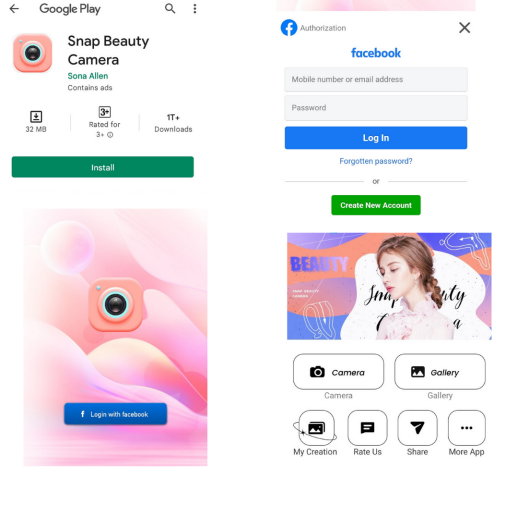
Figure 4: facebook stealer trojan snap beauty camera(crowdstrike, n.d.)
3.1.3 Mitigation
User awareness is must to minimize and mitigate the risk of these types of malware. Individuals must not provide any credential to a program that appears strange to them and must read the user review before downloading.
When the Play Store detects a problem that appears to be suspicious, it is instantly removed. Machine learning techniques are also used to detect malicious apps and trojans. Static, dynamic, heuristic and similarity analysis, reports generated by third parties, signatures, Developers connection, safetynet, and other tools are some of the technologies used by Google Play to distinguish malicious and non-malicious apps. Malware can also be detected using different antivirus software.
3.1.4 Summary
This trojan is injected into a fake malicious app where the user is forced to login to a fake system(facebook) in order to get the data. The interface used in those fake apps looks the same to the facebook login interface which gives user’s more confidence in the fake system. PlayStore automatically detects these types of trojans. However, it is very difficult to detect apps that are installed from unauthorized sources.
3.2 Mobile Banking Malware
3.2.1 Background
Baking Malware are suspicious applications that steal/collect data of finance, banking and e-payment related information. It can be anything ranging from customer’s details, banking information to protected password which is later used in online fraud.
3.2.2 Issue Identification
In most cases, these malware are made with a fake copy of the original banking app’s interface. The malware hides the original one as a result when the user enters the credential on a fake app, the credential is collected. Nowadays, that malware can also read and hide messages received to the mobile which makes it easier to find the one time transaction password and hide money transactions message.
BRATA, an acronym for Brazilian Remote Access Tool Android, is one of the Remote Access Tools that obtains banking information from users in Brazil. It was originally released in Brazil in 2018 and quickly spread over the world as a banking trojan. Initially, it could acquire banking data from users in real time via mobile phones, but it now has advanced features such as data erasure after an attack,ability to monitor the mobile device by using VNC and keylogging, device tracking using GPS and many more.
The attacker sends a message to the target’s phone, encouraging them to download the BRATA-containing app. In some cases, attackers call the targets to encourage them to download the app in order to make it appear legitimate. After downloading the software, the attacker takes over the victim’s phone and steals all of the victim’s financial information, including username and password. One time transaction password is also sent to the attacker’s server where they can do the banking transaction.
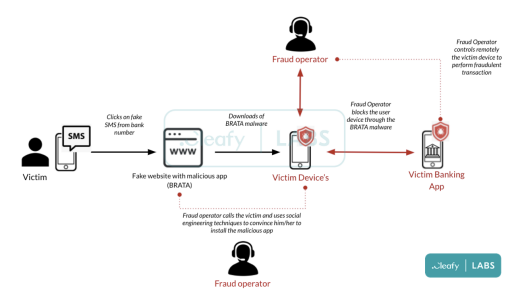
Figure 5: Mobile Banking Malware (cleafy, n.d.)
Ghimob and TROJAN-BANKER. ANDROIDOS.AGENT are also a trojan that steals online banking usernames and passwords, as well as the user’s bank card information.
3.2.3 Mitigation
To avoid this type of RAT, users should avoid downloading programs from untrustworthy sources and pay attention to the permissions the apps request.Any unauthorized app should not be given accessibility or administrator permissions. Although these types of apps are not available on the Play Store, we should avoid any apps that seek for extra permissions and appear suspicious.Risk assessments are also continuously being done by banks technical team and developer to mitigate the risk.The Google Play Store’s machine learning algorithms are also being improved to detect these types of malwares. As soon as malware is found in these types of apps, they are removed from the play store. Different antivirus software and defenders can be used to detect these types of malware.
3.2.4 Summary
Banking malware exploits and mis-appropriates banking data. This type of fraud can be done using different techniques including making fake copies of the banking app’s interface or asking extra permission from the user and accessing the victim’s mobile phone.These trojans are automatically detected by PlayStore. However, detecting programs installed from illegitimate sources is quite tough.
4. Conclusion
One of the most serious risks today is mobile malware. Malware can attack any operating system and comes in a variety of forms. Risktool, trojans, RATs, rootkits, keyloggers, and other mobile malware are examples. Mobile virus targets older phones with outdated security rather than newer phones with updated security. Even if the quantity of mobile attacks is decreasing compared to previous years, the attacks are becoming more powerful. Mobile phones are infected with a variety of malware. One of them is the facebook stealer trojan, which uses a login page that appears like Facebook’s official login page to harvest data from Facebook accounts, including email and IP address. This virus was discovered in a number of mobile apps before being removed by Google Play. Another type of malware is mobile banking malware, which collects financial, banking, and e-payment-related data such as customer information, banking information, and protected passwords to be utilized in online fraud. One example of a mobile banking malware is BRATA. The first line of mitigation is awareness among the users. Users must be educated on the various types of malware and their effects. Users must also be forced to update the apps on a regular basis. To detect malware, Playstore employs a variety of machine learning algorithms.The Google Play Store’s machine learning algorithms are also being improved to detect these types of malwares. To identify malicious Android apps, machine learning techniques such as logistic regression, classification and regression trees, random forests, and Naive Bayes can be used. This report explains the various types of malware in Android and how to identify them using various machine learning approaches.
More research is needed to improve malware detection techniques.
References
Afonso, V.M., Amorim, M.F. de, Abed Grégio, A.R., Junquera, G.B. and de Geus, P.L. (2014). Identifying Android malware using dynamically obtained features. Journal of Computer Virology and Hacking Techniques, pp.9–16.
Alzaylaeea, M.K., Yerima, S.Y. and Sezer, S. (2020). DL-Droid: Deep learning based android malware detection using real devices. United kingdom: Elseviwe Ltd.
Belal, A. (2017). MALWARE DETECTION TECHNIQUES FOR Mobile Devices. College of Information Technology, Hebron University.
cleafy. (n.d.). Mobile banking fraud: BRATA strikes again | Cleafy Labs. [online] Available at: https://cleafy.com/cleafy-labs/mobile-banking-fraud-brata-strikes-again [Accessed 26 Apr. 2022].
Colaco, C.W., Bagwe, M.D. and Bose, S.A. (2020). DETECTION OF MALICIOUS ANDROID APPS USING MACHINE LEARNING TECHNIQUES. International Journal of Trendy Research in Engineering and Technology, 4(7).
crowdstrike (n.d.). What is Mobile Malware? | Definition, Types, Prevention. [online] crowdstrike.com. Available at: https://www.crowdstrike.com/cybersecurity-101/malware/mobile-malware/.
Duraipandian, Dr.M. and Vinothkanna, Mr.R. (2019). MACHINE LEARNING BASED AUTOMATIC PERMISSION GRANTING AND MALWARE IDENTIFICATION. Journal of Information Technology and Digital World, 01, pp.96–107.
Milosevic, N. and Dehghantanha, A. (2017). Machine learning aided Android malware classification. Computers & Electrical Engineering, pp.266–274.
PaloAltoNetworks (n.d.). What is Malware? [online] Palo Alto Networks. Available at: https://www.paloaltonetworks.com/cyberpedia/what-is-malware#:~:text=Malware%20(short%20for%20% E2%80%9Cmalicious%20software.
securelist. (n.d.). Mobile malware evolution 2021. [online] Available at:
Mobile malware evolution 2021
previous [Accessed 26 Apr. 2022].
Senanayake, J., Kalutarage, H. and Al-Kadri, M.O. (2021). Android Mobile Malware Detection Using Machine Learning: A Systematic Review. Basel,Switzerland: mdpi, pp.2–34.
Xu, Z., Ren, K., Qin, S. and Craciun, F. (2018). CDGDroid: Android Malware Detection Based on Deep Learning Using CFG and DFG. College of Computer Science and Software Engineering: College of Computer Science and Software Engineering.